Table of Contents
In a recent webinar, Michael Honeycutt, Product Marketing Manager at Corero Network Security, sat down with Raj Vadi, Senior Solutions Engineer at Corero Network Security, to explore the evolving threat landscape of Layer 7 DDoS attacks. As cybercriminals shift their tactics from traditional volumetric floods to more sophisticated application-layer assaults, organizations need to understand both the risks and the solutions available to protect their digital infrastructure.
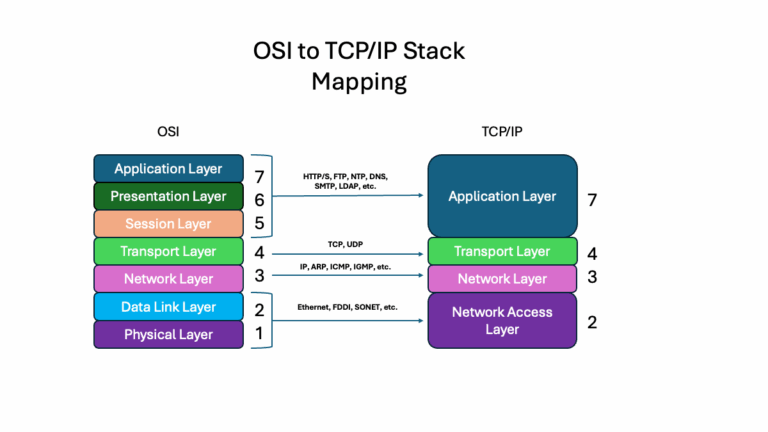
Understanding the OSI Model and Layer 7
Before diving into modern attack vectors, it is essential to understand where Layer 7 fits within network architecture. The OSI (Open Systems Interconnect) model consists of multiple layers, each serving a specific purpose in how data transits across networks.
Think of these layers as a series of envelopes, one within another, each adding its own address information with final layer carrying the data:
- Physical and Data Link Layers: Handle the network interface card and physical transmission
- Network Layer: Provides logical addressing (IP addresses) to route data between machines
- Transport Layer: Defines protocols and services through port numbers (like port 80 for HTTP)
- Application Layer (Layer 7): Contains the actual data being transmitted
When you request a web page, the data you receive represents the application layer. This is where protocols like HTTPS operate, and it is increasingly becoming the target of sophisticated attacks. TCP/IP predates OSI, and hence the mapping of layers, in a backport of the OSI model.
The Evolution of HTTPS and TLS
Today’s internet communications rely heavily on HTTPS (HTTP Secure), where the “S” indicates an additional encryption layer provided by TLS (Transport Layer Security). This protocol preserves data confidentiality between two endpoints—such as your browser and a banking server—ensuring that everything in between remains encrypted.
The development of TLS and its predecessor, SSL, enabled the massive commercialization of the internet by making secure online transactions possible. However, this same technology has become both a protection mechanism and an attack vector.
Why Attackers Target Layer 7
For the past 15-20 years, DDoS attacks primarily focused on network and transport layer floods—massive volumes of traffic designed to overwhelm infrastructure. These attacks exploited a fundamental characteristic of internet protocols: the lack of sender verification, like how the postal system does not always verify return addresses.
Today, several factors have shifted attacker focus to Layer 7:
Improved Network-Layer Defenses: Advances in mitigation technologies, cloud infrastructure, and hyperscale capabilities have made traditional volumetric attacks less effective, even though they still occur at massive scales (approaching 100 terabits).
Higher Impact with Lower Volume: Application layer attacks do not require terabits of traffic to be effective. A modest number of requests can bring down servers because each request forces the server to:
- Establish a connection
- Perform TLS handshakes
- Decrypt traffic
- Process the request
These operations are computationally expensive, especially the public key cryptography involved in TLS.
Evasion of Traditional Defenses: Most Layer 3 and Layer 4 mitigation technologies do not inspect encrypted application data, allowing malicious traffic to slip through while appearing legitimate at lower layers.
Real-World Attack Patterns
Modern Layer 7 attacks have evolved into multi-vector campaigns. Organizations often mitigate network-layer floods, only to discover their services remain degraded. Upon deeper inspection, the culprit is frequently malicious application-layer traffic hidden within HTTPS requests.
These attacks manifest through botnets—compromised IoT devices with default credentials that become unwitting participants in coordinated assaults. While the data volume remains modest compared to network floods (perhaps a few kilobits per request), the processing burden on servers is substantial.
The Corero Approach: Selective Inspection Without Bottlenecks
Traditional application security solutions often become reverse proxies for all traffic, creating potential bottlenecks. Corero takes a different approach:
Edge Mitigation: Initial filtering occurs at the network edge for volumetric attacks, using techniques like blackholing based on IP addresses or traffic anomalies.
Intelligent Selection: Rather than decrypting all traffic, Corero’s solution uses network-layer intelligence to identify suspicious sources, then selectively terminates and inspects their TLS connections.
Dynamic Blocking: Sources identified as malicious are placed in a temporary “jail”—blocked for a defined period. Repeated offenses extend the blocking duration, while legitimate traffic experiences no latency increase.
Symmetric Deployment: For effective Layer 7 mitigation, the solution requires symmetric traffic flow (seeing both inbound and outbound traffic) and can be deployed in-line, either physically or logically.
Deployment Flexibility
Corero’s solution accommodates various infrastructure models:
- Service Provider Edge: Mitigation at the carrier level for protocol-layer attacks
- Enterprise On-Premise: In-line appliances for smaller to mid-sized organizations
- Scrubbing Centers: For larger enterprises requiring dedicated traffic inspection
- Hybrid Models: Combining cloud-based bulk mitigation (such as through Akamai partnerships) with on-premise inspection for encrypted traffic
Key Differentiators
Not a Web Application Firewall: Unlike WAFs that focus on intrusions, API attacks, and injection vulnerabilities, Corero specializes in preventing malicious request floods at the application layer—a fundamentally different security challenge.
Selective Decryption: Rather than becoming a performance bottleneck by terminating all traffic, the solution samples and inspects only suspicious sources based on behavioral analysis.
No Certificate Offloading Required: For service provider deployments, the solution can operate without the complexity of managing customer certificates.
Operational Simplicity: Designed for service providers with lean operations teams, the solution features policy-based configuration and can be fully managed by Corero’s expert team.
The Managed Service Advantage
One of Corero’s most compelling value propositions is its fully managed service option. Layer 7 attack mitigation requires specialized knowledge and constant vigilance. Rather than burdening IT teams with complex configurations and incident response, Corero’s experts provide proactive monitoring and rapid response during attacks.
This approach has resulted in a 97% customer retention rate—a testament to both the solution’s effectiveness and the quality of support provided.
Looking Ahead
As the threat landscape continues evolving, attackers will undoubtedly develop new techniques to exploit application-layer vulnerabilities. Organizations must move beyond traditional volumetric DDoS protection to address these sophisticated, low-volume, high-impact attacks.
The key is finding a solution that provides comprehensive protection without introducing operational complexity or performance degradation. By understanding both the technical nature of Layer 7 attacks and the architectural requirements for effective mitigation, security teams can make informed decisions about protecting their critical applications.
Want to learn more?
This is the first installment in our three-part series on Layer 7 security. Stay tuned for deeper dives into web application protection and emerging mitigation strategies.
To discuss how Corero can address your specific security challenges, connect with our specialist team for a consultative assessment of your infrastructure needs.


