Table of Contents
Introduction
Trying to make a simple phone call is hard if you don’t have the number. Trying to get to a website without the corresponding IP address is even harder. Fortunately, Domain Name System (DNS) servers operate behind the scenes to make that connection for you. DNS allows you to access websites and applications using domain names and URLs rather than complex IP addresses. However, that pivot role also makes DNS servers attractive targets for DDoS attacks.
In this blog, we’ll dig into the role of DNS in network operations, explore the types of DNS DDoS attacks, and provide guidance on DNS protection solutions to help you mitigate risk.
DNS DDoS Protection
DDoS (distributed denial-of-service) attacks are responsible for more than 50% of attacks according to Verizon’s 2024 Data Breach Investigations Report. One of the ways threat actors use DDoS attacks is to target DNS servers with an overwhelming volume of traffic until their performance suffers and they eventually crash. Let’s explore the important role DNS servers play and the harm these attacks cause to networks, organizations, and users.
The Critical Role of DNS in Network Operations
Every web transaction involves a DNS service that translates a user’s search into an IP address that seamlessly gets us to our desired destination. It’s the lifeline that connects people and organizations – keeping the economy moving forward and vital services flowing including healthcare, education, energy, government, and media.
Given the critical role of DNS in connectivity, it’s no surprise that DNS servers are prime targets for DDoS attacks. Threat actors are intent on inflicting damage, and bringing down a DNS server is an efficient way to inflict damage on millions of people. Here are a few examples:
- One of the most notable DNS DDoS attacks happened in 2016 when Dyn, a major Domain Name Service (DNS) provider, became the victim of a 1 terabit per second DDoS attack – a record at that time. The attackers leveraged a botnet built on Mirai malware to flood the DNS provider with traffic and rocked the industry as the impact was felt across the U.S. and Europe. The attack knocked Dyn’s services offline and, with it, numerous high-profile websites including HBO, Twitter, Reddit, PayPal, Netflix, GitHub, and Airbnb.
- The Spamhaus attack is another example of a DNS DDoS attack. Initially, threat actors targeted the organization. When they realized the organization was protected, they ultimately shifted their focus to the organization’s network providers and were successful in disrupting and slowing down internet traffic in Europe and impacted millions of users for several days.
- More recently, a Russian botnet was discovered in 2023 that offers DDoS-as-a-service to pro-Russian hacktivists. The botnet was used to launch DNS DDoS attacks to disrupt connectivity to medical institutions in the U.S., Portugal, Spain, the U.K., Germany, Poland, Finland, and the Netherlands.
Risks Posed by DDoS Attacks Targeting DNS Infrastructure
A DNS DDoS attack can harm the targeted network and its users in several ways, including:
- Service disruption. The primary aim of a DNS DDoS attack is to disrupt targeted networks or website services and make them unresponsive to legitimate user requests.
- Increased latency. DNS DDoS attacks can also cause delays in server response times, resulting in slow page load times and similar lags.
- Lost revenue: The longer the length of downtime, the longer services aren’t available to the business and its customers, which results in loss of revenue to the organization.
- Reputation damage: When users don’t have reliable access to the services they need, an organization’s reputation can take a significant hit, which can result in an increase in customer churn.
- Recovery costs: In addition to the costs of bringing services back online, recovery costs can also include forensic analysis and upgrades to defenses. Depending on the impact on customers there may also be costs associated with regaining trust and loyalty.
- Follow-on attacks. Threat actors can use a DNS DDoS attack as a way to disguise their real intentions. While the security team is distracted by addressing the denial of service, the threat actor shifts their focus to compromise other systems for other types of attacks such as data breaches and ransomware.
Types of DNS DDoS Attacks
There are several types of DNS DDoS attacks. What sets them apart are the specific techniques they use and how they function.
- DNS Flood Attacks attempt to exhaust the resources of a DNS server by flooding it with a massive volume of valid but spoofed requests. Since the requests appear to be legitimate, the server responds to each request until its resources become exhausted and the server goes offline, taking the targeted organization’s internet access with it.
- DNS Amplification Attacks aim to bring down DNS servers by triggering an amplified response. Attackers send a large number of small DNS queries from a spoofed source IP address to a targeted server. The server then replies with a huge volume of responses that overwhelms its network capacity.
- DNS Water Torture Attacks take a low and slow approach, sending a constant stream of small, legitimate-looking DNS queries to the server. The relentless stream of queries disrupts legitimate traffic and erodes server responsiveness, eventually causing service disruptions.
Mitigating DNS DDoS Threats
DNS servers work seamlessly to connect people to websites or applications instantly. However, behind the scenes the process involves four different types of DNS servers working independently in different capacities to process each search: Recursive DNS servers, Root name servers, Top level domain (TLD) name servers, and Authoritative name servers. This complex ecosystem of interconnected servers makes it difficult to detect and mitigate DNS DDoS attacks without disrupting legitimate users and requires a high degree of expertise.
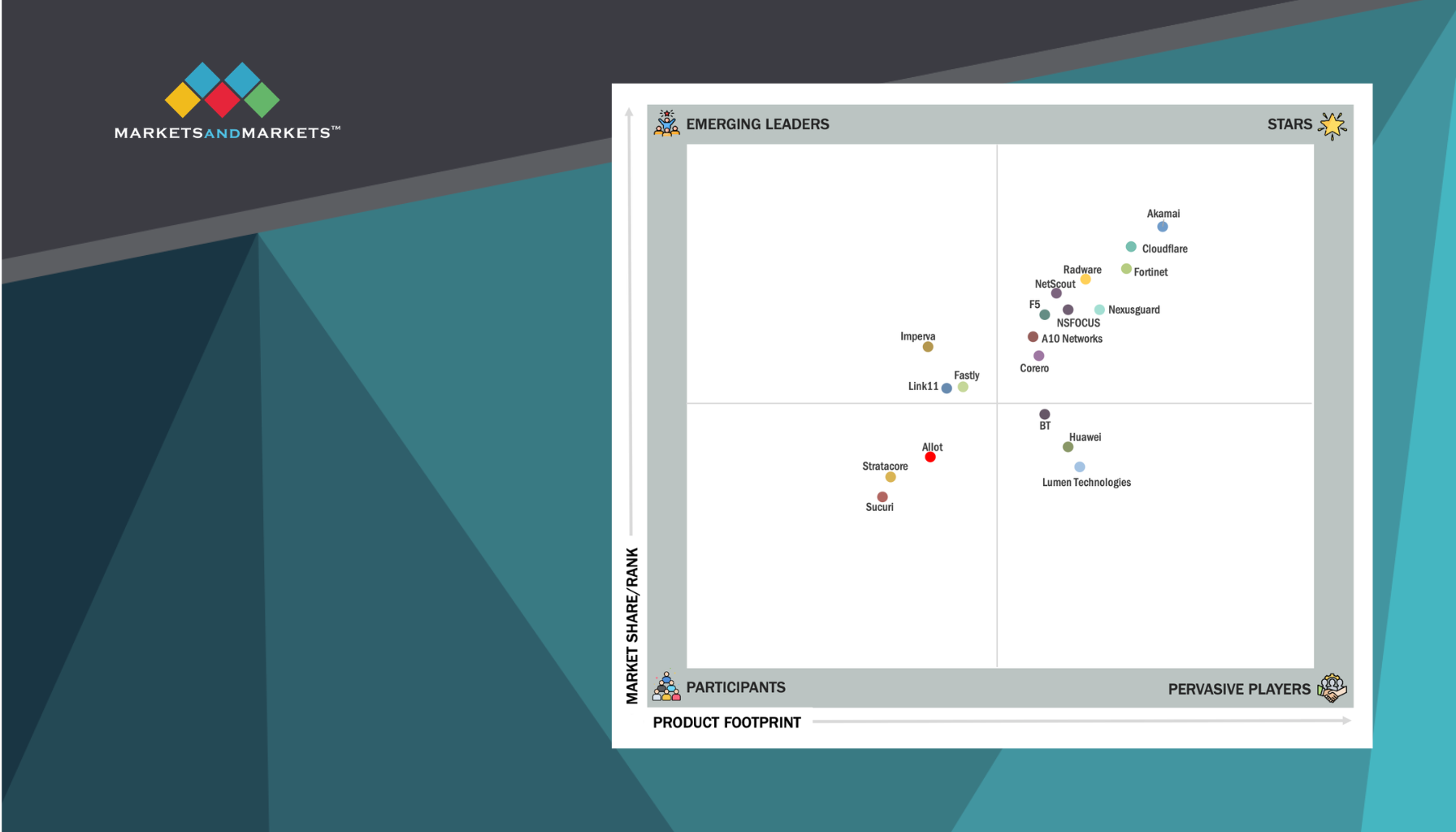
Entirely dedicated to DDoS protection, Corero has a strong track record of mitigating the gamut of DNS DDoS attack types for organizations across diverse industries, including telecommunications, hosting, and ISP operators.
Advanced DNS DDoS Protection Solutions
Advanced DDoS protection coupled with real-time threat intelligence to stay ahead of emerging threats, provides uninterrupted service availability even in the midst of a DNS DDoS attack. Adaptive solutions flex to meet your bandwidth needs, providing a solid foundation for growth. Comprehensive DDoS protection can also defend against follow-on threats including data leakage, ransomware attacks, and other malicious activity that can harm your business.
Managed Services and 24/7 Support
Alternatively, a fully managed DDoS protection service with round-the-clock support, attack-time services, and reporting, available on a subscription basis, can also provide peace of mind. Organizations have confidence that their digital assets are protected against the full spectrum of evolving and growing DDoS attacks, including DNS flood, DNS amplification, and DNS water torture attacks, while keeping internal IT teams focused on core business operations.
Final Thoughts
Every web transaction involves a DNS service that translates a user’s search into an IP address that seamlessly gets us to our desired destination. However, behind the scenes the process involves four different types of DNS servers working independently in different capacities to process each search, which adds to the complexity of protecting against DNS DDoS attacks.
Over the last 20 years, some of the most high-impact DDoS attacks were a result of a DNS DDoS attack that knocked high-profile websites offline or brought down internet operations across entire countries for days.
Given the criticality and complexity of DNS infrastructure and the sophistication and rapid growth of DNS DDoS attacks, organizations should consider implementing an advanced DDoS protection solution, or a fully-managed service. Either way, DDoS protection coupled with intelligence to stay ahead of emerging threats, provides uninterrupted service availability even in the midst of a DNS DDoS attack. Comprehensive DDoS protection can also defend against follow-on threats attacks. Visit our threat intelligence research center for more information on DDoS defense in depth.