
Table of Contents
Network infrastructures are complex and each is unique. This article takes a look at the information system layers in a network’s infrastructure, the role they play in securing against DDoS attacks, and the best practices for a multi-layer DDoS defense.
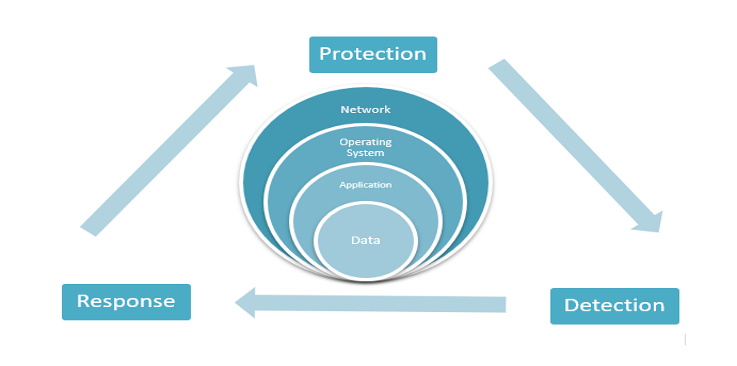
The Four Essential Information System Layers
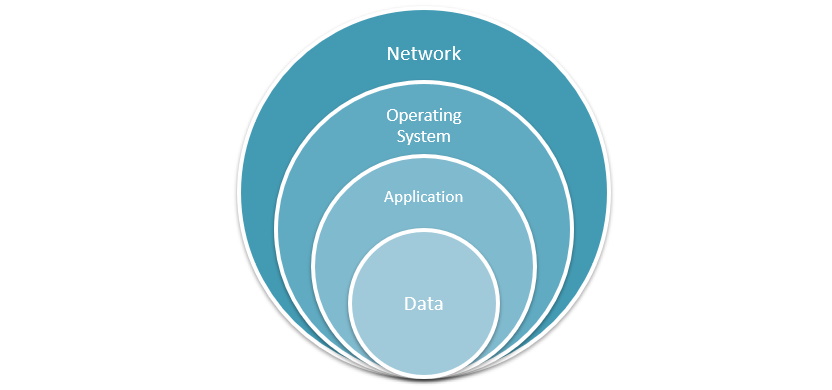
Network infrastructures can be very different from one to another depending on different business needs and setup requirements. No matter the infrastructure, there will always be at least four information system layers involved. These are:
It is very important to understand how these layers work together before beginning to design security controls around these layers.
- Network: routers, switches, firewalls, wireless access points, etc. The first layer in the information system is responsible for establishing communications between devices or segments.
- Operating System: Microsoft Windows, Linux, Unix, Mac-OS, Android, iOS, etc. The OS allows users to install applications, store, and interact with data. Two devices do not have to run the same OS in order to talk to each other if they can support and agree on the same network protocol.
- Application: web servers, databases, emails, etc. The application layer can work in client mode or server mode and is responsible for serving and allowing user interaction with data or querying and asking server applications for data.
- Data: billing statements, health records, account credentials, etc. Data is the most crucial layer out of the four. After going through the network layer, interacting with the OS, talking to the server/client application, users can retrieve, modify, upload, delete, or change data as desired.
Defense in Depth
Defense in depth is a strategy that refers to multiple layers of security protection implemented at different layers of an information system.
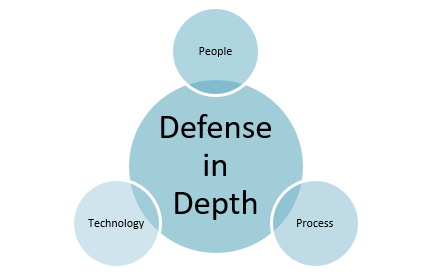
- People – Having people with the proper training and resources is a key factor in any successful security program.
- Process – Documented processes in place ensure continuous protection for the concerned information system and data.
- Technology -While technology is critical in network defense, it is only one aspect of an effective security system.
Without the right people to implement the technology, and processes in place to ensure the technology is working correctly, any security strategy will eventually collapse.
What functions should be performed at each layer?
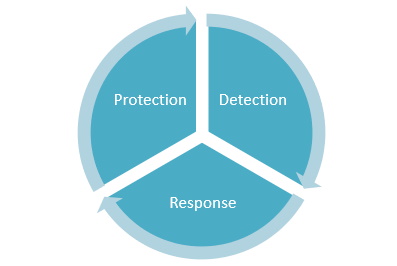
Protection, detection, and response are the three elements that the people, process, and technology should deploy and maintain to ensure maximum security.
Protection
There are many security solutions within the scope of network protection: firewall, application firewall, anti-virus, IPS, and encryption, to name a few. Protection solutions can help prevent intrusion attempts from entering your network and reaching the data layer.
Security is not all about protection. Even if protection solutions were able to work without fail, additional security elements would be unnecessary. In the real world, there will be situations where protection solutions will fail – for example zero-day threats that are yet unknown. This is when detection becomes important.
Detection
When your security protection fails, detection security controls such as NIDS, HIDS, and log analyzers will prove vital. Being hacked is bad, but it’s worse when the hack goes undetected; so having a detection solution that sends an alert in the event of an attack, outage, or other unexpected incident is critical. For DDoS, if an attack occurs that causes an outage and goes undetected, there will be no information to mitigate future attacks.
As the old saying goes, ‘better late than never’ and when it comes to security alerts, late really is better than never.
Response
If an event occurs, protection fails, and an alert is sent, it only helps if there is a security control procedure in place to respond immediately.
For example: money is stored in a safe with a complicated lock (Protection). A camera is installed to monitor and alert if there is motion when someone comes close to it (Detection). If there is not someone to monitor the camera and call the police, the thief can break your lock to get money inside. It may not be a day or a month, but in time locks can be broken. With no one to respond and stop the thief, the money can be taken.
The DDoS Attack
DDoS may come from many sources, and its sole purpose is to bring down targeted services by flooding traffic to that service or saturating bandwidth.
Attackers can flood traffic to a service directly by TCP flood (SYN flood, RST/FIN flood), UDP flood, or ICMP flood. A DDoS attack can also be performed indirectly using a reflection attack by spoofing target server IP addresses and sending requests to public reflectors that then send amplified responses to overwhelm targets with large amounts of unsolicited traffic.
Refer to this document for more attack types: https://www.corero.com/blog/glossary/
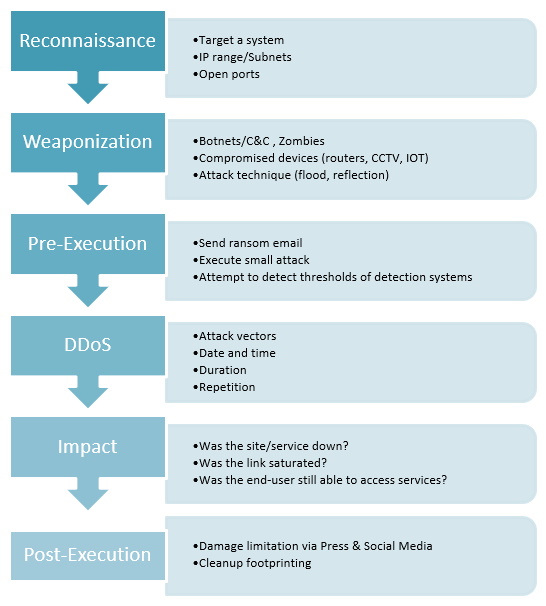
The phases of a DDoS attack:
Applying Defense in Depth to DDoS solutions
A complete solution should consider people, process, and technology in relation to all four essential layers, along with the three security controls of protection, detection, and response.
This article focuses on technology at the network layer as it pertains to DDoS protection. Each organization will have different requirements and processes in place and may have people who are trained with the necessary skillsets that meet the organization’s needs.
Next, let’s look at how the protection, detection and response functions can be applied at the network layer, to help defend against DDoS threats.
Protection
The network layer is the frontier to other information system layers. Most common DDoS attacks can be mitigated at this layer. Deploying a DDoS defense system is only the first step and there are important questions that should be answered: Is network defense deployed in the right network topology? Are thresholds too low and blocking the legitimate traffic? Is the scale of the solution suitable for the needs of the organization?
Even all the answers are “yes”, there is still a chance that attack traffic can get through. Blocking a large amount of bad traffic can still result in some leakage, causing issues for users. What can help to identify any the leakage and mitigate it?
Detection
DDoS solutions must be able to send alerts to various channels when an event is detected, after all, when you’re under attack, it’s not the dashboard that wakes you up, but THE ALERT.
If reading a log line-by-line, the attack might have finished and already caused issues before the right information can be found to mitigate the attack. Charts and dashboards are powerful tools for analysis to quickly visualize traffic and get a clear picture of what is happening during attack time.
A detection engine should also be implemented to detect abnormal traffic for zero-day/new vector attacks.
As a part of the SmartWall solution, here at Corero, we utilize Splunk to ingest and analyze large amounts of data in real time. This allows for immediate detection and alerting of anomalous traffic that can impact a network.
Response
To investigate an attack and any leakage of bad traffic, logs and events are the key aspects for analysis. Having a DDoS defense system that provides adequate data on the attack, not only for the current timeframe, but for past attacks, can aid in response.
It’s also important to remember that even with a good DDoS protection solution in place, that can prevent most DDoS attacks and send useful log data to dashboards and charts, attacks are constantly changing. Without response, detection is useless. Response procedures must be in place to handle situations that arise when protection plans fail.
Conclusion
Being the victim of a DDoS attack is bad, but it is worse when these attacks go unnoticed or can’t be mitigated.
Solutions that focus heavily on a single aspect of security, only the protection aspect, can cause the whole security deployment to collapse. Having a well-rounded security solution that has the key components of protection, detection, and response along with the right people, processes, and technology is the best way to secure a network against DDoS threats.
New attack vectors are always a challenge and require more advanced techniques to block effectively without causing harm to legitimate traffic. Corero’s SecureWatch Managed Services allow organizations to outsource all, or a portion, of the SmartWall deployment to our security engineering experts. The cycle of Protection (or Mitigation), Detection and Response is maintained by Corero and kept up to date with the growth of botnet and new DDoS vectors as they develop.
