
A closer look at the DDoS attack that took Blizzard’s services offline and ruined hardcore runs for WoW players
Table of Contents
It was a period of intense frustration for Blizzard gamers on March 22nd, 2025. Further insights suggest the digital siege weapon used was a botnet, adding another layer to understanding the disruption.
The Background
The DDoS attack interrupted a game with some hardcore characters, and this is an important part to understand.
In World of Warcraft (WoW), “Hardcore” refers to a specific, high-stakes ruleset, often played on dedicated servers, where character death is permanent. If your character dies for any reason, it cannot be resurrected and is effectively lost forever, making survival the absolute priority and changing gameplay dramatically. This means that if a DDoS attack makes it difficult to control your character for even a minute, the player could lose countless hours of playtime spent on that character.
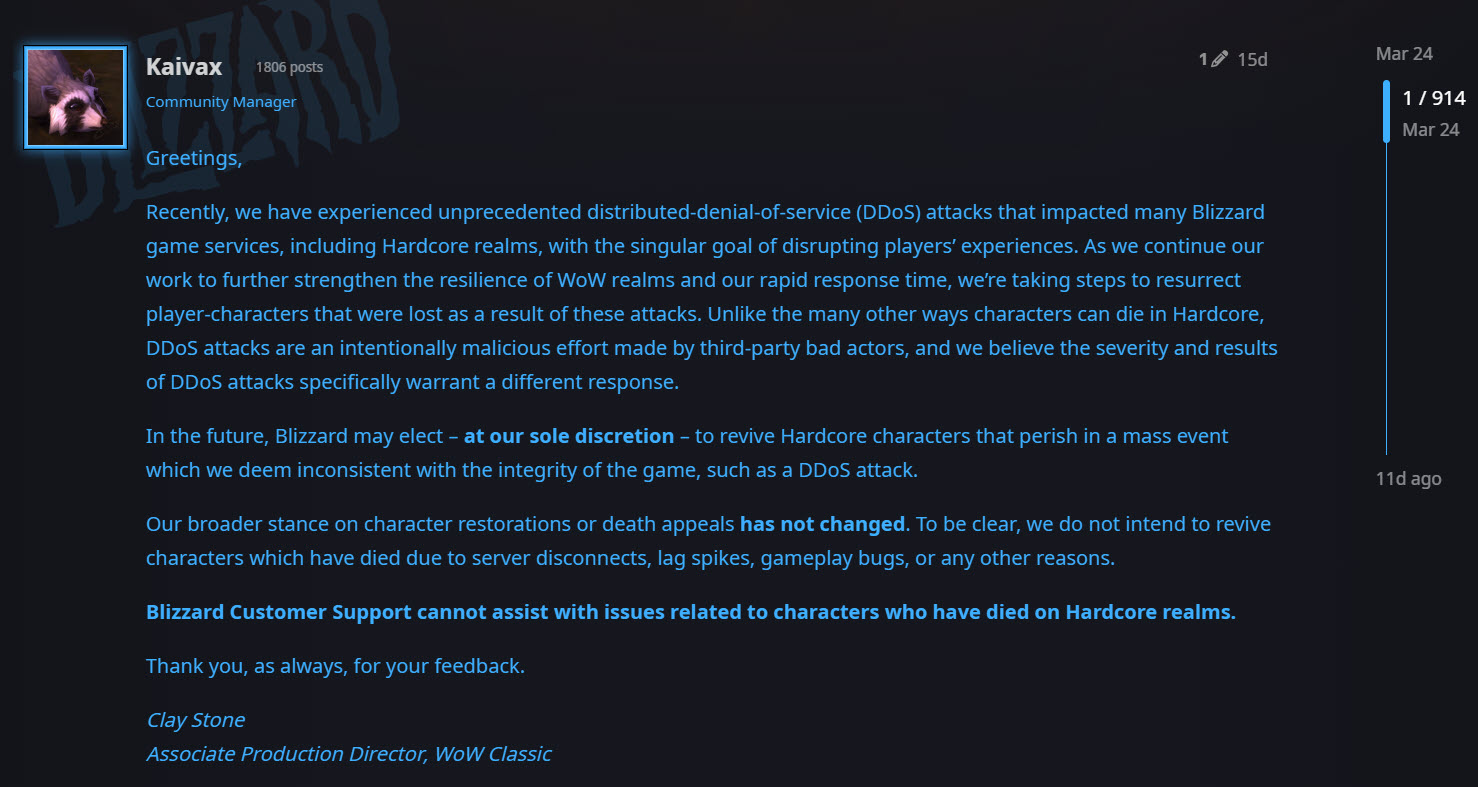
This attack was different, as some very high-profile players were streaming live game-play and were affected. Blizzard announced that it would restore characters affected by the attack on March 22nd. One of their community managers said, “Unlike the many other ways characters can die in Hardcore, DDoS attacks are an intentionally malicious effort made by third-party bad actors, and we believe the severity and results of DDoS attacks specifically warrant a different response.”
Analyzing the Attack
At 5:30pm EST, Blizzard confirmed there was a DDoS attack affecting their service. By checking forums and other methods a closer estimation of the start time was around 5:15pm.
By using the time given by the WoW players, and indirect analysis of traffic data, Corero Network Security was able to find a common vector being used by several bots. These bots were sending large TCP PSH ACK packets to a few Blizzard IP addresses on a common WOW gaming port (3724) during the attack time. This traffic type at high volume was not seen from any sources during non-attack times.
Next Steps
In an update about the attack, Blizzard stated, “We are continuing to strengthen the resilience of WoW realms and the speed at which we respond to character deaths on Hardcore realms caused by DDoS attacks.”
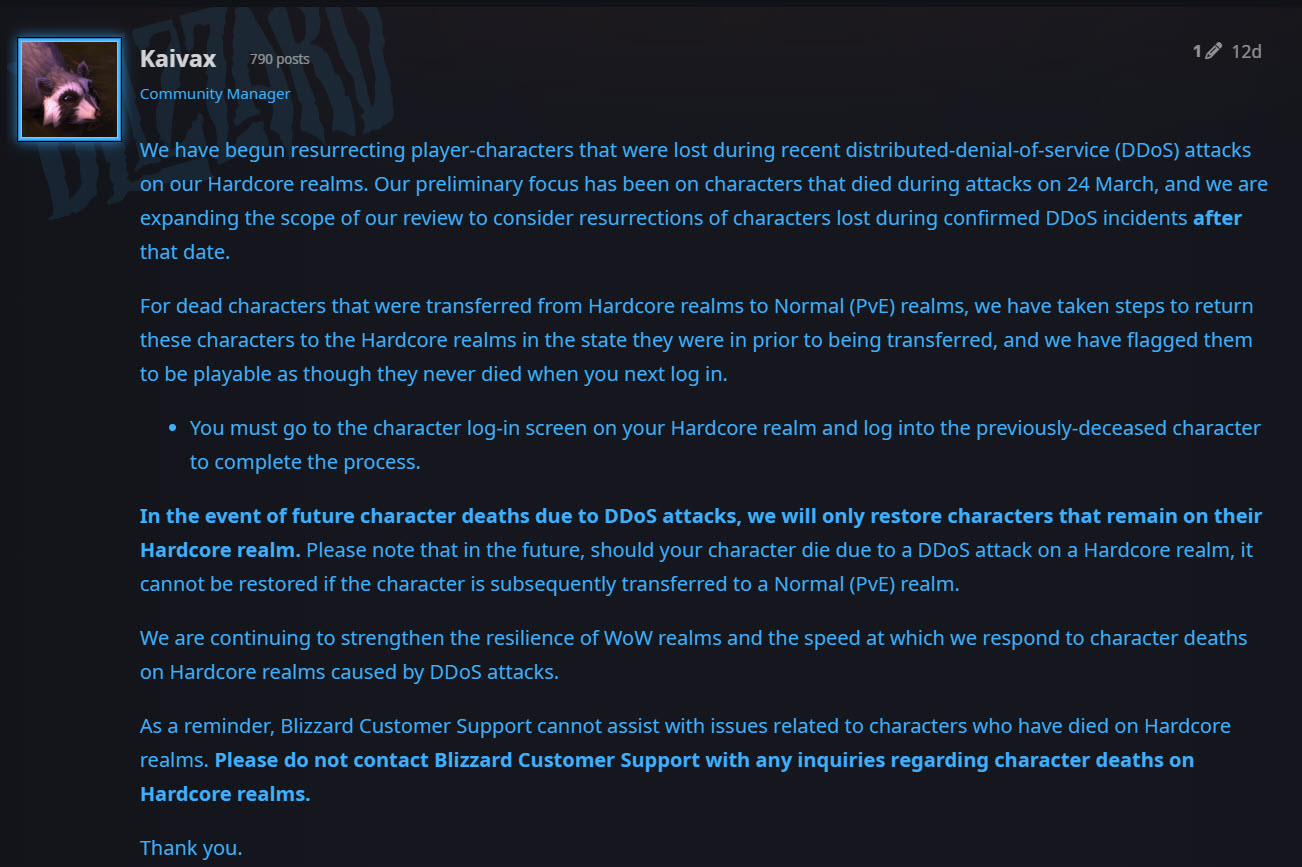
While the in-game actions Blizzard has undertaken are a matter of debate, most network engineers in the gaming community agree that extremely large DDoS attacks will continue and better defenses are needed.
How to Improve the In-Game Experience
DDoS mitigation begins with visibility. Analytics leads to differentiation of the good vs bad traffic. Once that is done, then a device capable of performing that differentiation at line rate is needed.


