Table of Contents
When your infrastructure faces a multi-terabit DDoS attack, every second counts. Just last week, we saw one of the most persistent and high-volume DDoS assaults on one of our clients–lasting several hours and using a mix of advanced attack vectors.
In this post, we’ll walk you through our real-time response–how we detected the threat in real time and ultimately neutralized the attack without service disruption. Whether you’re managing a global network or just curious about how large-scale mitigation works, this is a look into the reality of modern DDoS defense at terabit scale.
Attack Analysis
In this attack campaign, the goal was straightforward: consume all available bandwidth to the point where genuine traffic would be dropped or delayed beyond usability, creating a denial-of-service condition through sustained network congestion.
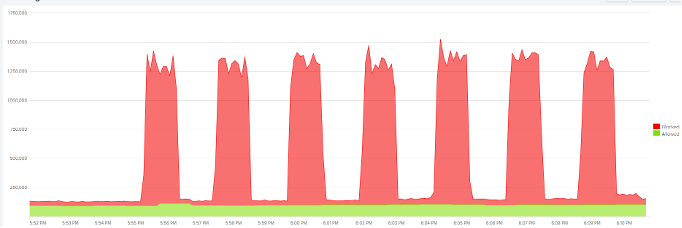 DDoS attack mitigated by Corero Graphic" />
DDoS attack mitigated by Corero Graphic" />1.5 Tbps DDoS attack mitigated by Corero
The primary attack vector was a UDP flood using large packets, designed to consume as much bandwidth as possible. Source ports, destination ports, and payloads were randomized, making it difficult to block traffic by relying on traditional signature-based filters.
This DDoS attack originated from globally distributed sources, indicating a large-scale botnet spanning multiple countries and autonomous systems. Our analysis revealed that over 19,000 devices participated in the attack, with the majority being compromised DVR and NVR systems – commonly exploited in IoT-based botnets due to outdated firmware and weak security configurations. The involvement of compromised IoT devices like DVRs and NVRs, combined with the use of randomized ports and high-volume UDP floods, aligns closely with tactics commonly associated with Mirai-based botnets.
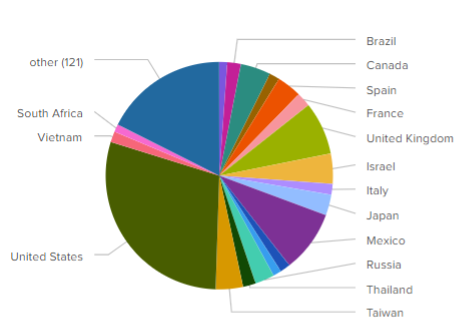
Distribution by source country
We routinely observe Tbps DDoS attacks that are intense but are short-lived. However, this incident stood out–the attack sustained high traffic volumes for more than eight hours, making it one of the most persistent volumetric assaults we’ve seen to date.
How Corero Mitigates Multi-Tbps Attacks
High Performance System – Multiple Locations – Zero Downtime
To effectively mitigate large-scale attacks, the system must operate at very performant levels. Just as important, legitimate traffic must continue to flow uninterrupted during mitigation. The ability to block malicious traffic without impacting real users is a key measure of robust defenses.
The attack targeted an internet service provider (ISP) and Corero devices were deployed across multiple regions, automatically activated to mitigate the malicious traffic in real time. This coordinated response ensured that the customer’s infrastructure remained operational and accessible throughout the attack.
Preparation Before the Storm
Our threat research team is continuously monitoring the threat landscape to identify emerging DDoS attack vectors. By proactively developing and deploying countermeasures before attacks reach our customers, we stay ahead of adversaries. Leveraging our DDoS Intelligence Service, the team can distribute these protections across the infrastructure–standing ready even before the first packet of an attack arrives.
Defense-In-Depth Strategy
Security architectures that rely too heavily on a single layer of defense expose risk and fragility. If that layer fails, the entire system can collapse. A resilient DDoS mitigation strategy must follow a defense-in-depth model—one that integrates protection, detection, and response, supported by the right people, well-defined processes, and robust technology. This layered approach is essential to withstand today’s sophisticated and persistent threats.
Conclusion
In today’s threat landscape, DDoS attacks are no longer rare events. They’re persistent, evolving, and increasingly complex. Defending against them requires more than just reactive measures. It demands a proactive, intelligent, and layered approach–backed by high-performance systems, global infrastructure, and a dedicated team that stays one step ahead of attackers. At Corero, we combine real-time mitigation, high performance system, and continuous threat research to ensure our customers stay online, even in the face of terabit-scale attacks. Preparedness, agility, and depth of defense are the keys to resilience.


