Table of Contents
Introduction
Computer networks are made up of different technologies that interrelate to enable communication. A reference model, or framework, serves as a guide to help technology vendors and developers ensure that their technologies (hardware, software, operating systems, connections, and more) interoperate effectively to enable network communications.
In this blog, we’ll look at one of the most common models used today, the OSI model. You’ll learn about the importance of OSI model, the functions of each of its seven layers, how data flows through the layers, and its pros and cons. Finally, we’ll explore how DDoS attacks target different layers of the OSI model, how to recognize an attack, and how to defend your organization.
What is the OSI model?
In 1984, the International Organization for Standardization (ISO) introduced the Open Systems Interconnection (OSI) model. Developed based on learnings from earlier models, the OSI model is an international standard that serves as a basis for how technology vendors can describe the role of their technologies in enabling interoperability and communication and how they interact with other components.
Today, the OSI model is one of the most common models used by companies and developers around the world. It helps companies define their standards and protocols for designing and creating technologies while maintaining interconnectivity, and it makes it easier to troubleshoot failed components and security issues.
What are the 7 layers of the OSI model?
The OSI model is organized around seven layers with each layer having specific functions to perform and working with the layer above and below it.
The seven layers model helps visualize and explain how the different components for network communication interconnect to ensure smooth data flow. As show in the figure below, the model is described starting at the top, or application layer, where the end user interfaces with the network via software. It culminates at the bottom, or physical layer, where connectivity over wires or cables and the transmission of raw data happens.
The 7 Layers of the OSI Model
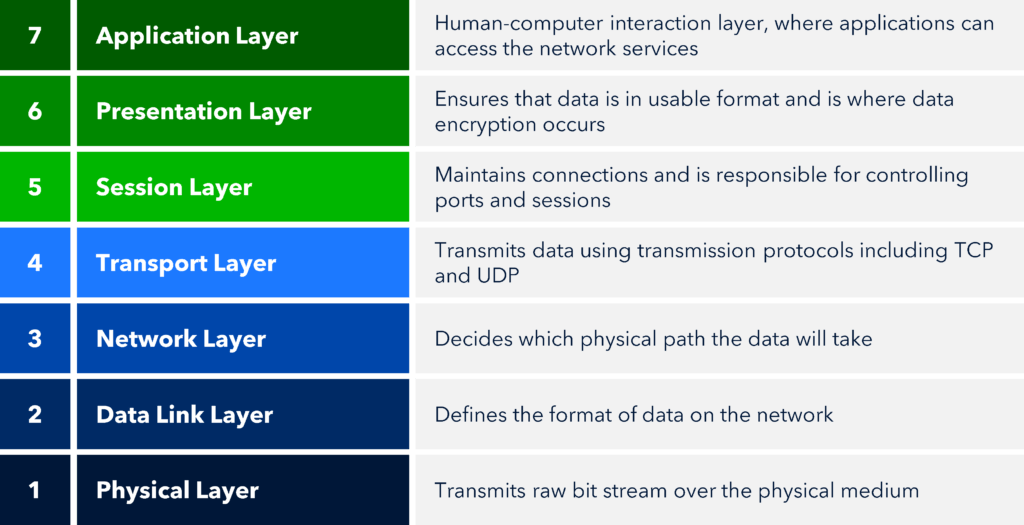
Let’s take a closer look at each of the seven layers of the OSI model.
Layer 7: Application layer
At the top of the seven-layer OSI model is the application layer. End users interact at this layer to transmit data via applications to the network. Examples of applications include web browsers, e-mail, and remote file transfer that use protocols including Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), and File Transfer Protocol (FTP) to transfer data.
The application layer in the OSI model ensures effective communication between these applications and different computing systems and networks.
Layer 6: Presentation layer
Layer six is the presentation layer and it serves the following primary functions.
- Acts as the translator of the data received into a format so that it can be readable by the application layer and used by the session layer.
- Encrypts and decrypts data before transmitting it over the network to ensure secure communication.
- Performs data compression to reduce the overall size of the data transferred and enhance speed and efficiency of transmission.
In short, the presentation layer ensures that data is in a useable format and is secured via encryption.
Layer 5: Session layer
The session layer in the OSI model maintains connections and is responsible for controlling ports and sessions.
It does this by opening and closing communication sessions and managing the time intervals for data transfer to ensure efficiency and avoid wasting resources.
During a session it manages data streams using checkpoints and enables data synchronization. For example, when large data files are being sent, it can break the data down into smaller chunks. If a transmission becomes interrupted due to a network or system failure, the transmission can pick up where it left off once the failure is resolved and transmission doesn’t have to start all over again.
Layer 4: Transport layer
The transport layer in the OSI model ensures the reliability and completeness of each message exchanged. It uses data segmentation, data flow controls, and error-checking mechanisms to ensure the connection between the sender and the receiver can handle the amount of data being transferred and the speed of the transmission, and that the data is complete.
For example, it divides the data from the sender into smaller segments and reassembles it at the receiver side so that it can be read. The transport layer also regulates the speed when sending files so that even if the device sending the data has a good network connection, if the receiving device does not then it will reduce the speed to accommodate the slower connection. The transport layer also checks for errors in the data and if the data is incomplete, it will issue a request to resend the data.
The transport layer transmits data using transmission protocols including transmission control protocol (TCP) and user datagram protocol (UDP).
Layer 3: Network layer
The primary function of the network layer is to decide which physical path the data will take. This is referred to as packet routing – choosing the best possible route that connects two different networks to ensure efficient data transfer and applying internet protocol (IP) addresses for routing purposes.
It receives data segments and breaks the segments down into smaller packets at the sender side to enable it to move into and through other networks efficiently. On the receiver side, Layer 3 reassembles the data.
Layer 2: Data link layer
The main functions of the data link layer of the OSI model are to define the format of the data on the network and to move data into and out of the physical link in a network.
It breaks the data packets from Layer 3 into frames so that they can be transmitted to the physical layer. It also manages connections between two different network nodes, handles error control, and terminates connections when a session is complete.
Layer 2 of the OSI model is divided into two sub-layers: media access control (MAC) and logical link control (LLC). The MAC layer encapsulates data frames transmitted through the network-connecting media such as wires or cables. The address resolution protocol (ARP) translates IP addresses to MAC addresses and updates headers of created frames to establish communication. In situations where the data transmission fails, LLC helps manage packet retransmission.
Layer 1: Physical layer
The last layer of the OSI model is the physical layer that sends and receives data in the form of raw bit streams (ones and zeros) over a physical hardware and network components such as cables, switches, or routers.
More specifically, Layer 1 picks up bits from the sender end, encodes them into a signal, sends the signal over the network, and decodes the signal at the receiver end. Essentially, Layer 1 is the key to communicating data bits across network devices through physical media.
How data flows through the OSI model
When you sit down at your computer or grab your phone to send an email or order something online, you’re transferring information from your device through the seven layers of the OSI model. Data flows down the seven layers from your end, and then flows back up the seven layers on the receiver’s end.
The step-by-step process of the OSI model goes like this:
- Application layer: Applications create the data
- Presentation layer: Data is formatted and encrypted
- Session layer: Connections are established and managed
- Transport layer: Data is broken into segments for reliable delivery
- Network layer: Segments are packaged into packets and routed
- Data link layer: Packets are framed and sent to the next device
- Physical layer: Frames are converted into bits and transmitted physically
Along the way, each layer adds specific information to ensure the data reaches its destination correctly. Upon arrival, these steps are reversed so that the recipient can read the information.
It’s hard to imagine all this happening in the blink of an eye – but it does. A simple example of what goes on behind the scenes when you send an email brings this to life.
- You open your email application like Gmail or Outlook, write an email, and hit send. (Layer 7 of the OSI model)
- The email application prepares the data for transmission, including formatting the data, encrypting it, and compressing it for transmission. (Layer 6 of the OSI model)
- A communication session is set up to establish the connection between the sender and the receiver on the internet. (Layer 5 of the OSI model)
- Email data is divided into smaller segments and flow and error controls are applied to ensure the data is transmitted reliably and completely. (Layer 4 of the OSI model)
- Segments are broken down into packets that are addressed and routed to ensure the fastest path to the recipient. (Layer 3 of the OSI model)
- Data packets are encapsulated into frames, MAC addresses are applied, and packets are transmitted to the physical layer. (Layer 2 of the OSI model)
- Frames are transmitted as raw data over physical hardware and network components (cables or WiFi) to the recipient. (Layer 1 of the OSI model)
When the email reaches the recipient, the process is reversed, and the email content is reassembled and decrypted so the recipient can read it in their email application.
The importance of the OSI model
The OSI model was first introduced 40 years ago and is a widely used standard to allow standalone systems to communicate reliably and efficiently. It remains essential today for several reasons:
Enables a shared understanding of complex systems. Engineers use the OSI model to organize and model complex networked system architectures. Decomposing a system into smaller parts makes it easier to conceptualize complex systems.
Accelerates research and development. When working on a networked system, engineers can quickly get an understanding of how the system should communicate, depending on which layer they are developing for. They can also use repeatable processes and protocols to accelerate development.
Fosters standardization. Engineers don’t have to understand every aspect of the model in order to use it. They can focus on the systems they are designing and leverage the model to standardize network communication development without prior knowledge of the highly complex systems they need to communicate with.
Makes it easier to isolate networking vulnerabilities and security issues. Whether one person is having trouble with their laptop or thousands of people are impacted by a website being down, the OSI model helps identify the issue faster and avoid a lot of unnecessary work. The layers allow you to isolate network issues and focus on vulnerabilities and security issues based on the layers they impact without disturbing the entire model. Each layer can be secured, optimized, and troubleshooted independently.
Suitable for cloud-first environments. Even though it was developed decades ago, the OSI model remains relevant today as it helps detect security threats throughout an organization’s technology stack.
Helps create an inventory of physical assets, security resources, and applications. The OSI layers allow you to create an inventory of all your assets and applications and gain a better understanding of where your data resides – in the cloud or on-premises. This information helps you refine your security policies and make more informed security investment decisions.
Allows for updates to standard OSI models. Some technology companies have customized or updated their OSI models with cloud services in mind. This flexibility allows you to enhance the security of your networking environment as needed and speaks to the staying power of the OSI model.
Useful for equipment manufacturers. Standards for interoperability and communication enable hardware manufacturers to create and configure their devices so that they can communicate effectively irrespective of the other devices they may need to interoperate with.
Pros and cons of the OSI model
The OSI Model is not perfect, but there are many reasons why it is considered a standard model in computer networking and has persisted for 40 years.
Pros of the OSI model
- It standardizes network communications as each layer has fixed functions.
- It helps users and operators of networks determine the required hardware and software to build their network and gives them confidence that those products will interoperate.
- It helps with troubleshooting by identifying which network layer is causing an issue so operators can focus on that layer.
- It supports connectionless, as well as connection-oriented services. Connectionless services enable a message to be sent from one endpoint to another without prior arrangement. Users can take advantage of connectionless services when they need faster data transmissions over the internet and the connection-oriented model when they’re looking for reliability.
- It has the flexibility to adapt to many protocols and to cloud-first and hybrid environments.
- Dividing network communication into seven layers makes it more adaptable and secure than having services bundled into fewer layers.
Cons of the OSI model
- It doesn’t define any particular protocol, but rather the tasks that protocols perform. This can result in diverse approaches to execution and create complexity.
- Seven layers can be complicated and hard for beginners to understand.
- Each layer in the model adds its own set of rules and operations which can make the process to use the model time-consuming and inefficient.
- Some services are duplicated at various layers, such as the transport and data-link layers.
- Layers can’t work in parallel; each layer must wait to receive data from the previous layer.
OSI model vs TCP/IP model
The transfer control protocol/internet protocol (TCP/IP) model and the OSI model are the most broadly used networking models for communication. They are similar in many ways, including:
- Both are logical models.
- Both define standards for networking.
- They each divide the network communication process into layers.
- Both provide frameworks for creating and implementing networking standards and devices.
- They enable one manufacturer to make devices and network components that can coexist and work with the devices and components made by other manufacturers.
- Both divide complex functions into simpler components.
However, there are also several differences between the OSI and the TCP/IP model which is why they continue to co-exist:
- TCP/IP was created by the U.S. Department of Defense (DoD) in the 1970s so it is older than the OSI model and already had an established following of users when the OSI model was introduced.
- TCP/IP model consists of four layers while the OSI model has seven layers. Layers 5, 6, and 7 of the OSI model are combined into the Application Layer of the TCP/IP model and OSI model layers 1 and 2 are combined into the Network Access Layer of TCP/IP protocol.
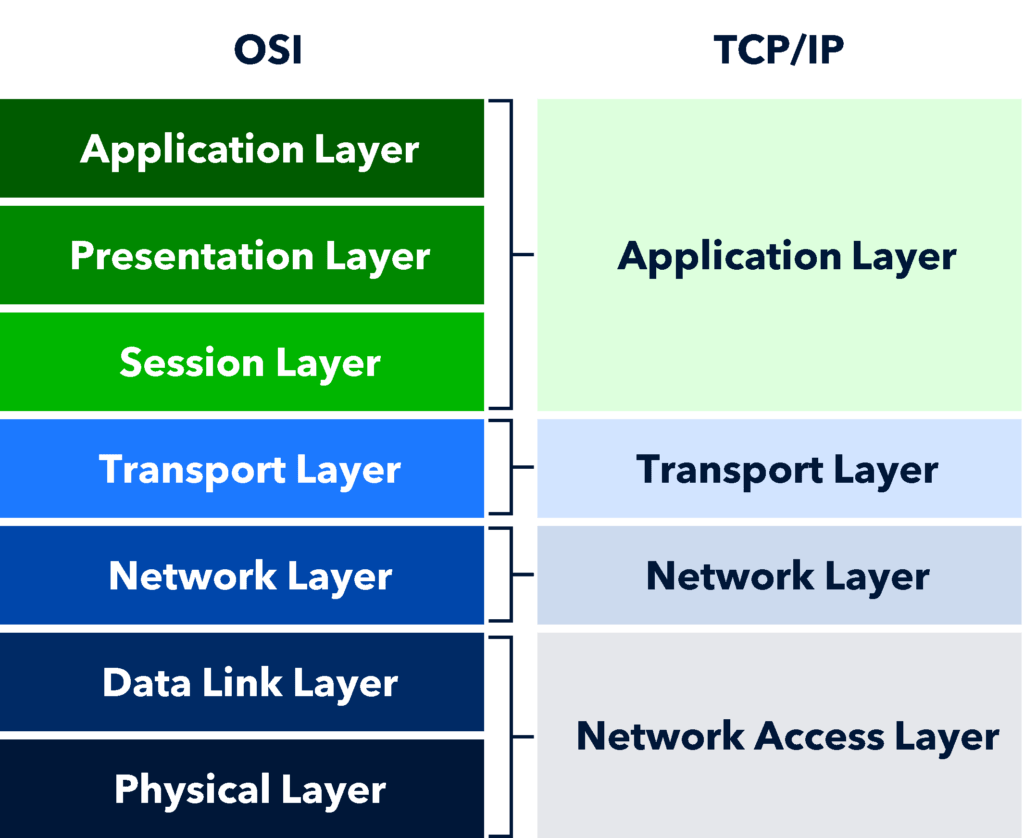
- The TCP/IP model is viewed as simpler and more practical for real-life networking due to its less strict layer boundaries and use of specific, standard protocols to interconnect network devices on the internet. While the OSI model is a more comprehensive and modular framework that describes all forms of network communication and is great for understanding concepts.
- The additional layers in the OSI model can add more complexity for implementation, but they also allow for easier troubleshooting and interoperability of protocols between layers, enhancing compatibility between different vendor products.
DDoS attacks and the OSI model
The ability to use the OSI model to safeguard computing systems has become even more important over the last decade as the volume and complexity of DDoS attacks have increased along with the layers and means by which they are being attacked.
For example, volumetric attacks that target Layers 3 and 4 flood a target’s network with a massive volume of traffic, overwhelming its bandwidth and causing service disruptions. Common volumetric DDoS attack types include SYN flood attacks, ICMP flood attacks, and UDP flood attacks.
Meanwhile, Layer 7 DDoS attacks target the application layer and seek to exploit vulnerabilities in the software or applications running on the server, causing a slowdown or complete service disruption, with HTTP/HTTPS flooding being one form of attack.
A significant benefit of the OSI model is that it enables defenders to focus on attacks to layers impacted without disturbing the entire model. Each layer can be troubleshooted and secured independently using a combination of best practices and technology, including content delivery networks, traffic monitoring and anomaly detection, rate limiting, load balancers, web application server connection limits, IP Blacklisting/Whitelisting, and DDoS protection.
Conclusion
Like Internet Relay Chat, and HTTP, the OSI model was created in the early days of network communications and remains a cornerstone of our connected experience. After 40 years, the OSI model remains a popular tool that provides a visual representation of the relationships between each communication layer and the function of each layer, starting with the application layer at the top and ending with the physical layer at the bottom.
The flexibility of the OSI model has enabled users to adapt it over the years to address the evolving needs of enterprise networks and expanding network communication requirements. And its role in standardizing network communication has helped equipment manufacturers create products that can interoperate as needed to ensure smooth communication. The flexibility and interoperability of the OSI model, combined with the granularity of the layers that make it easier to zero in on network issues and focus on vulnerabilities and security issues have contributed to the OSI model’s staying power.
The challenges of creating and maintaining cyber resilient network systems has increased as DDoS attacks against various layers of the OSI model have surged. Fortunately, using the OSI model, defenders can focus on attacks to layers impacted without disturbing the entire model so that each layer can be troubleshooted and secured independently. Additionally, DDoS protection provides uninterrupted service availability even in the midst of a DDoS attack and can protect you from attacks that threaten various layers of the OSI model.
FAQ
The OSI model is an international standard that serves as a basis for how technology vendors can describe the role of their technologies in enabling interoperability and communication and how they interact with other components.
Starting at the top where end user interaction happens, the seven layers of the OSI model are:
- Layer 7, the application layer
- Layer 6, the presentation layer
- Layer 5, the session layer
- Layer 4, the transport layer
- Layer 3, the network layer
- Layer 2, the data link layer
- Layer 1, the physical layer
The OSI model was first introduced 40 years ago and is a widely used standard to allow standalone systems to communicate reliably and efficiently. It remains essential today for several reasons:
- Enables a shared understanding of complex systems
- Accelerates research and development
- Fosters standardization
- Supports cloud-first environments
- Makes it easier to handle security issues
- Helps create an inventory of physical assets, security resources, and applications
- Allows for updates to standard OSI models
- Useful for equipment manufacturers