
Table of Contents
As more operators and service providers adopt Resource Public Key Infrastructure (RPKI) for Internet route validation, it’s important to understand the implications as it relates to DDoS protection in the cloud. Handled correctly, RPKI and cloud DDoS protections can work together to provide a more secure routing environment, but there are considerations for proper implementation.
What is RPKI?
Most IT and networking professionals, from enterprise to service providers, are familiar with Border Gateway Protocol (BGP). It has become the fundamental routing protocol for the internet, and a major backbone in how we have connected to each other all over the globe. Peering and routing advertisements allow resource holders to distribute their networks on the Internet, and influence routing decisions globally.
Unfortunately, the current BGP standards do not include a method in which to verify the authenticity and origin of these routing advertisements. This has allowed for a vulnerability to BGP Hijacking (accidentally or otherwise) in which routes which do not belong to the resource holder are advertised through unauthorized systems. Internet Routing Registry (IRR) has partially stepped in to help alleviate this potential by allowing providers to document policies and manage route objects, but ultimately IRR is a trust-based model and lacks true validation mechanisms.
This is where RPKI comes in. RPKI offers cryptographic validations, which are managed by the resource holders themselves through a Regional Internet Registry (RIR). While RPKI is a broad subject itself, two concepts are crucial when it comes validation:
- Route Origin Authorization (ROA): This is the signed object which contains the routing information authorized by the resource holder. It includes Prefix, Maximum Length, Authorized Origin ASN, and other relevant information.
- Route Origin Validation (ROV): This is a the process a router performs when receiving a BGP route and is configured for RPKI. It compares the received route information against the ROAs for the Prefix. Depending on the results, the route may marked as:
- VALID. This indicates the announced route matches an ROA
- INVALID. This indicates the route conflicts with an existing ROA, such as an incorrect Origin AS or incorrect Prefix Length
- UNKNOWN. This status indicates the route is not covered entirely by an existing ROA
These validation statuses are used by operators in routing policy to filter or change priorities on incoming route announcements. Most commonly, VALID and UNKOWN are accepted, while INVALID are completely blocked.
RPKI adoption is becoming more commonplace on the global internet. According to a MANRs article published May of 2024, over 50% of the IPv4 BGP Routes are now covered by ROAs according to the NIST RPKI monitor. Understanding how RPKI functions and how global operators use Route Origin Validation has become more essential than ever in the current industry.
RPKI and Cloud DDoS Protection
Cloud DDoS protection is a popular mitigation strategy for ensuring service continuity against volumetric DDoS attacks that risk bandwidth or resource saturation. This is most commonly accomplished by using BGP advertisements to redirect traffic through the cloud DDoS provider either on-demand or at all times.
As RPKI Validation becomes more common, it’s important to understand the implications of using a BGP-based cloud DDoS solution.
Most of these cloud DDoS services will include guidance or requirements for RPKI ROAs. This is important, as incorrect or misconfigured ROAs can at least reduce the efficacy of the cloud DDoS protection, or at worst cause actual harm to normal traffic.
There are two major considerations for RPKI and cloud DDoS:
- If the Cloud DDoS Solution announces your prefixes from their AS, you must ensure the prefix ROA includes their ASN as an authorized Origin. Failure to do so risks having RPKI Validating providers mark these advertisements as INVALID and not accepting them. This is less of a concern when advertising routes to a Cloud Provider to readvertise, as often the Origin AS remains your own.
- You must ensure your ROAs have the correct Maximum Length defined. Often, resource holders with on-demand cloud DDoS solutions advertise the most specific available route of the DDoS target, often a /24, to readvertise and redirect through the Cloud scrubbing center. If your ROA does not include this Prefix Length, it will likely be marked as INVALID upstream and will normally not be accepted globally, reducing or eliminating the benefit of the cloud DDoS service.
Conclusion
As the Internet evolves, security and safety is a top concern. RPKI and cloud DDoS protection can be used to protect your environments from potential risks and ensure service availability. Understanding these technologies and how they interact will arm you with the knowledge to create robust and secure networks and build a safer Internet across the globe.
Resources
RPKI ROV Deployment Reaches Major Milestone – MANRS
Resource Public Key Infrastructure (RPKI) — RIPE Network Coordination Centre
Route Origin Authorizations (ROAs) – American Registry for Internet Numbers
RFC 6488 – Signed Object Template for the Resource Public Key Infrastructure (RPKI)
Using RIPE Routinator to Check RPKI Validation
Checking the propagation and validity of your prefixes in RPKI is essential to maintaining proper object management. RIPE recommends the use of the ‘Routinator’ tool, which is accessible through a web UI to check the status of prefixes and optionally associated ASNs.
The Routinator tool may be found here: Routinator
When first accessing the tool, you’ll be presented with a prompt to input an IP or Prefix, and optionally an ASN. Entering an IP with the default options selected will infer the prefix length and perform a check against the inferred route.
For example, if entering 8.8.8.8 and clicking Validate, it will infer 8.8.8.8/24 and perform a check against that prefix and return the Origin ASN associated if found and report Validation status for the VRP (Validated ROA Payload). It will use the observed ASN in BGP.
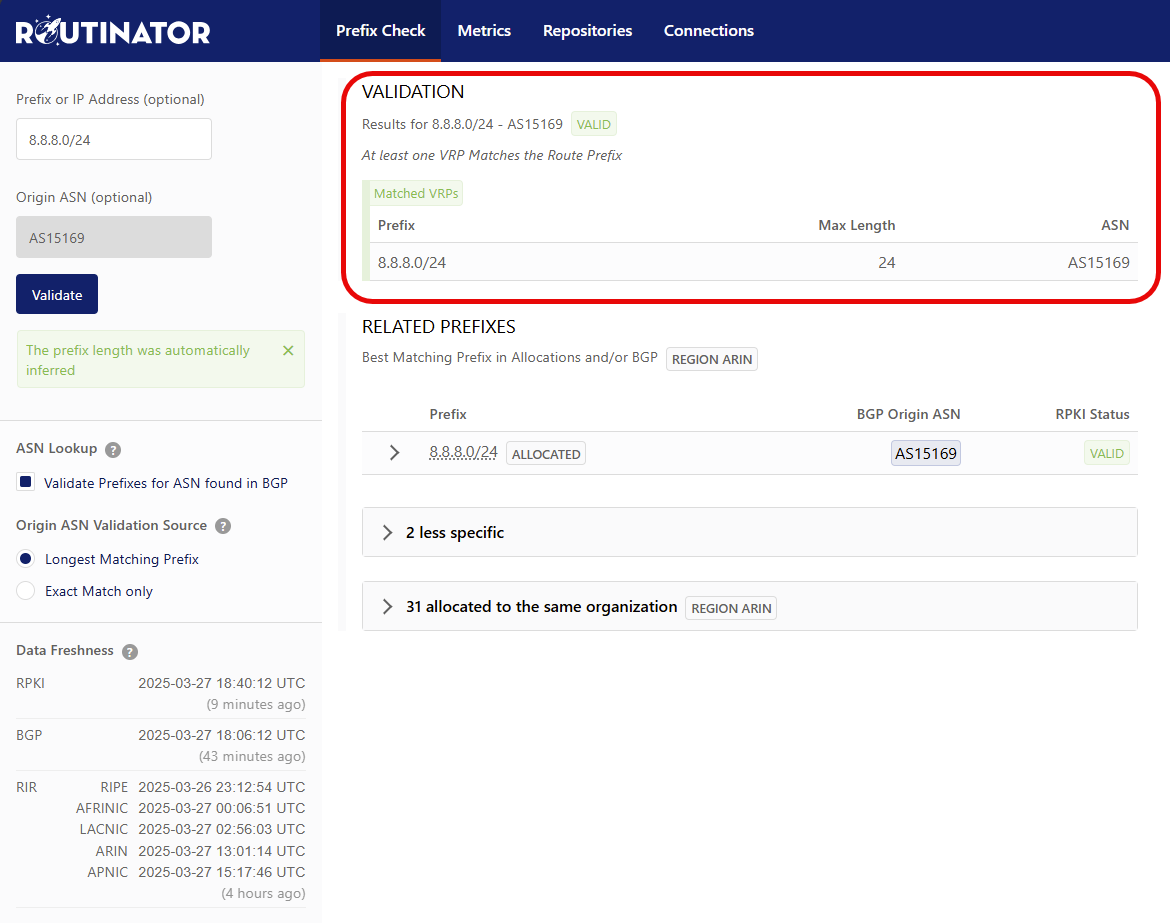
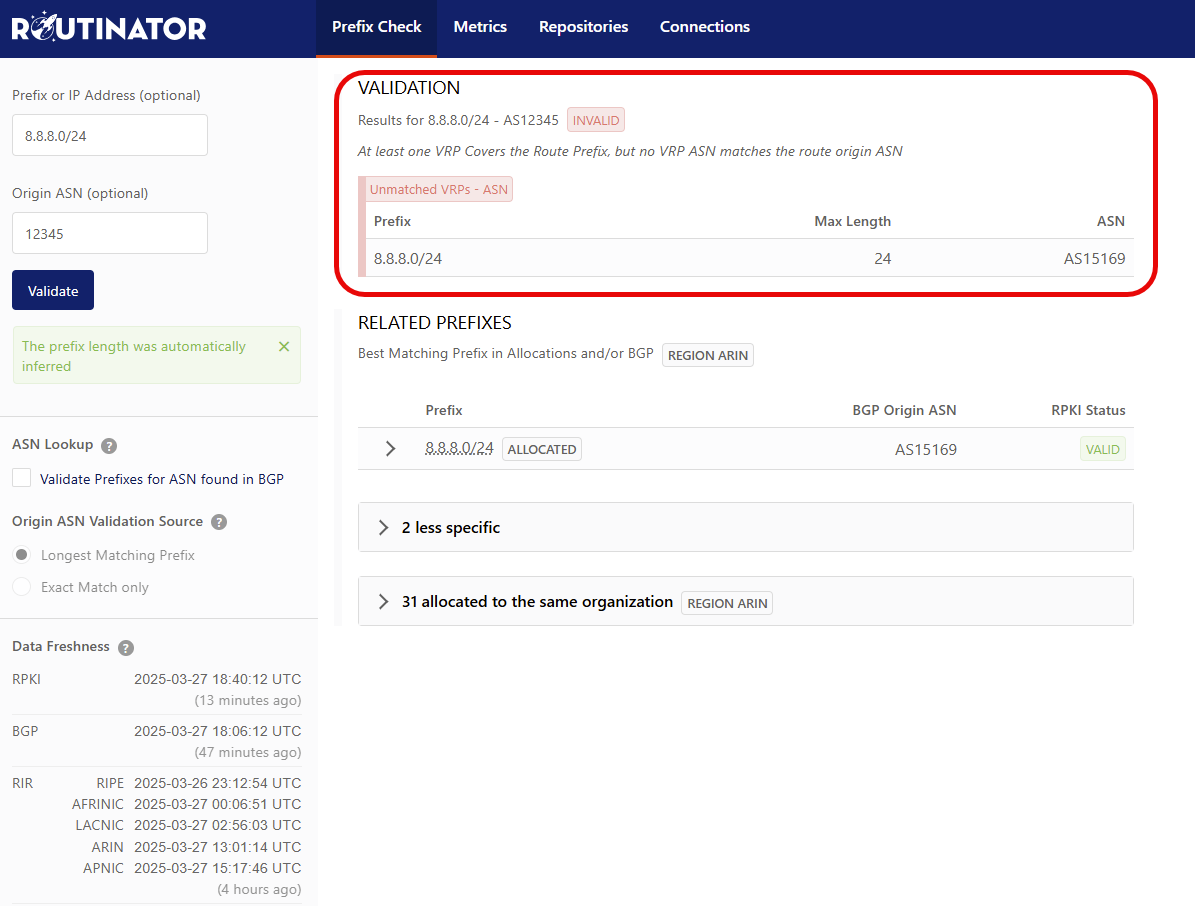
Using the optional Origin ASN Field you can specify an ASN to Validate against without having the tool look it up by what is observed in BGP. In this case, using a bogus ASN will report an INVALID status, as the Origin AS does not match the existing VRP.
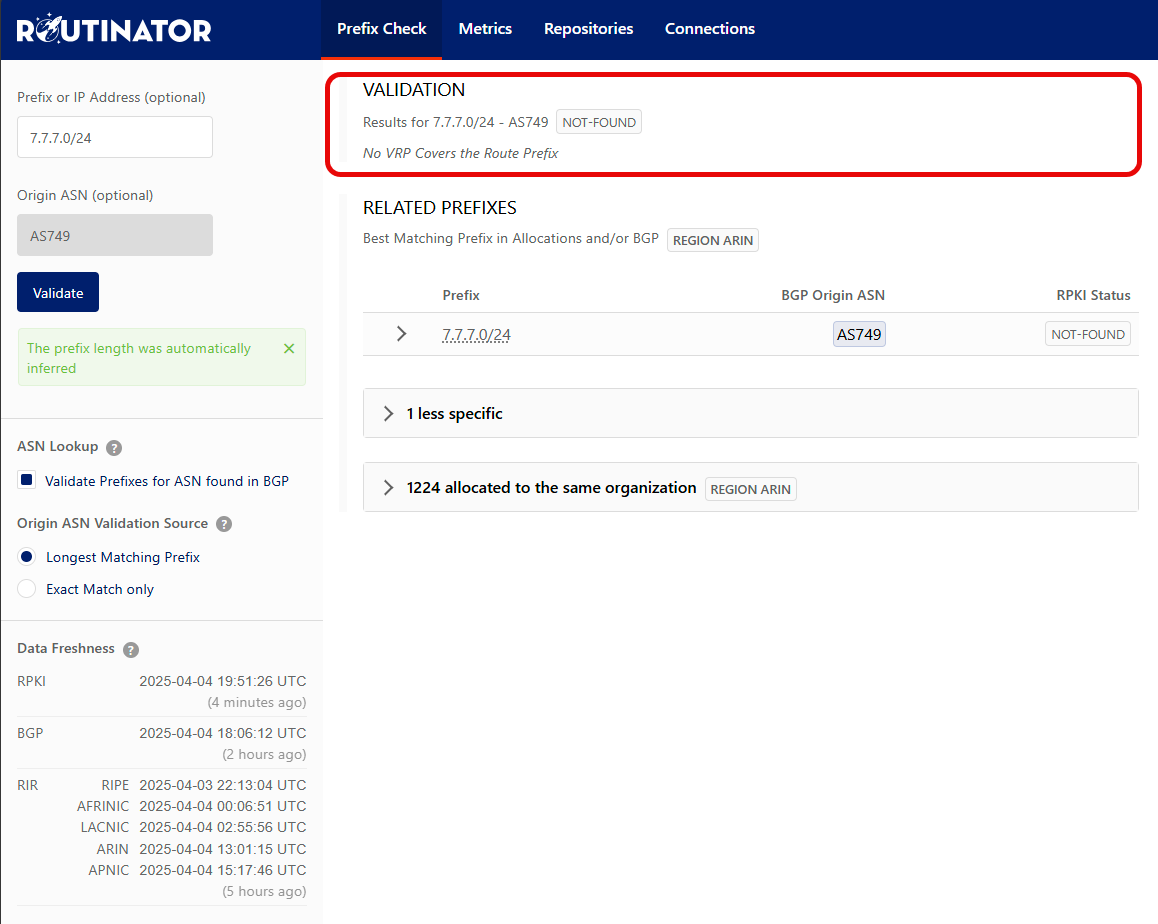
Searching for a valid route, but which does not have any ROAs configured will display a NOT-FOUND result, which is assigned an UNKNOWN status in router validation.
There are other tools available on the internet as well, such as CloudFlare’s RPKI Portal. Familiarizing yourself with RPKI tools and understanding the record management and validation processes involved will aid you in maintaining a safe, secure, and resilient network environment.


