
The Corero SecureWatch Threat-Intelligence team has observed a new example of cybercriminals creatively abusing the infrastructure of innocent organizations on the Internet, to target others with damaging DDoS attacks. This latest threat vector leverages Hikvision video devices exposed to the Internet, exploiting their Search Active Device Protocol (SADP), to launch reflective amplification DDoS attacks.
What is SADP?
SADP is Hikvision’s software for discovering their online devices, such as IP cameras and DVRs/NVRs and intended for use in a local network environment. The utility supports viewing device information, activating devices, editing a device’s network parameters, and resetting device passwords, etc. (1)
The protocol uses a multicast address of 239.255.255.230 and UDP port 37020 for sending and receiving control packets.
SADP is similar to WSD (Web Service Dynamic Discovery) and SSDP/UPnP (Simple Service Discovery Protocol/Universal Plug and Play). These protocols have been used in reflection amplification DDoS attacks for many years now, so it’s not that surprising when a new discovery protocol such as SADP emerges, that this soon gets exploited in a similar manner.
The attack in practice
Reproduction and detailed analysis of this attack was undertaken by the Corero SOC team in a controlled LAB environment.
With a single packet sent to a Hikvision device, the reflection can be successfully triggered. In amplification attacks, the technique is to send the smallest possible request and use a spoofed source IP address of the targeted victim. The objective is to solicit the largest response possible from the reflector to be sent to the target victim IP.
Below is the identified request that triggers the largest amount of response data:
<?xml version=”1.0″ encoding=”utf-8″?><Probe><Uuid>string</Uuid><Types>inquiry</Types></Probe>
In this example, a single 128-byte request creates a response of 1,013 bytes, resulting in an amplification factor of 7.9x, or 790%.
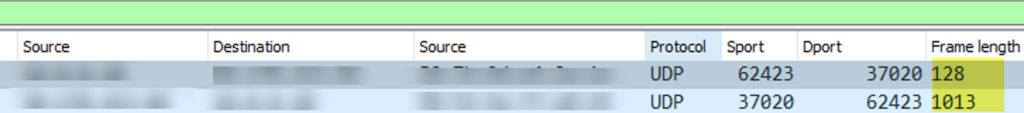
Figure 1: Frame Length of Request and Response packet
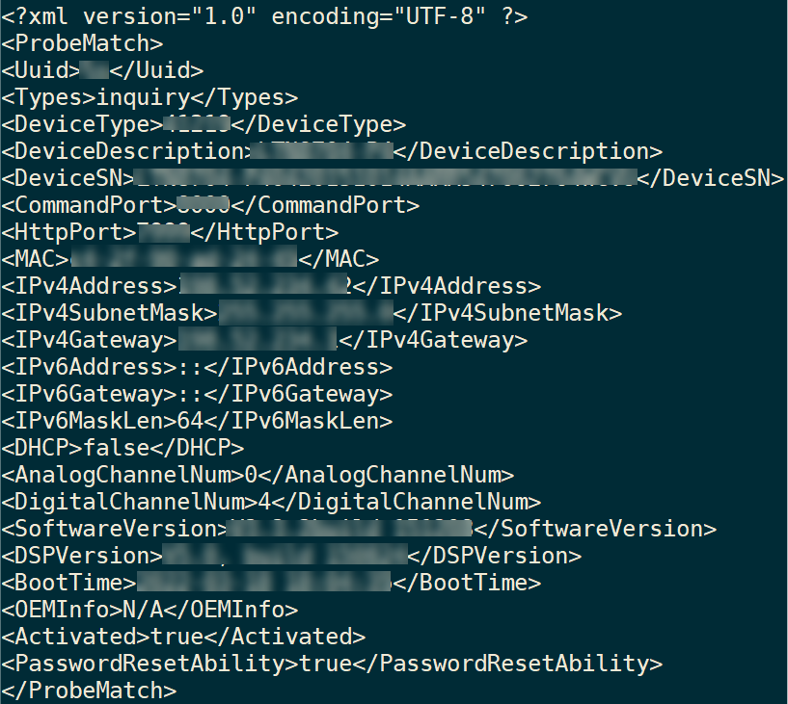
Figure 2: Sample of Response Packet
Potential number of reflectors
A Shodan search for Hikvision devices exposed to the Internet, shows approximately 4.5 million results. Not all are likely to have port UDP port 37020 exposed, but in one attack observed by Corero’s SecureWatch team, approximately 7,700 different Source IP addresses were recorded, which is a very substantial figure for a DDoS attack.
Why SADP?
The amplification factor of SADP is 8:1, which compared with other reflection DDoS vectors such as DNS, NTP, DVR, etc. is relatively low.
However, in September 2021 a critical vulnerability was identified which allows attacks to be launched via a command injection, sending messages containing malicious commands (CVE-2021-36260 (3)).
This has likely caused cybercriminals to pay increased attention to this vendor and the exploitable attributes of their devices, in order to help build botnet armies, or launching potentially damaging amplified reflection DDoS attacks, as we have recently seen.
Although the amplification factor is not as high as other recently discovered reflection vectors, such as T240PhoneHome and TCP Middlebox, the number of potential reflectors is impressive and further increases the opportunity for cybercriminals to launch DDoS attacks.
As cybercriminals discover these potential attack opportunities it increases their arsenal of possible reflectors, which can then be included in future multi-vector attacks.
How to defend SADP attacks?
Corero’s threat intelligence team expects this latest DDoS attack vector to be observed more frequently in the future. Fortunately, these attacks can be automatically detected and mitigated by the latest generation of DDoS protection solutions, such as Corero’s SmartWall ONE, which includes zero-day protection. Existing Corero customers are already being comprehensively defended from this latest DDoS vector, by our intelligent, automatic, heuristics-based, Smart-Rule signatures.
For over a decade, Corero has been providing state-of-the-art, highly effective, automatic DDoS protection solutions for enterprise, hosting, and service provider customers around the world. Our SmartWall® DDoS mitigation solutions protect on-premises, cloud, virtual and hybrid environments. If you’d like to learn more, please contact us.
References
- https://www.hikvision.com/en/support/tools/hitools/clea8b3e4ea7da90a9/
- https://www.forbes.com/sites/leemathews/2021/09/22/widely-used-hikvision-security-cameras-vulnerable-to-remote-hijacking/?sh=46dee3f02f31
- https://www.hikvision.com/en/support/cybersecurity/security-advisory/security-notification-command-injection-vulnerability-in-some-hikvision-products/security-notification-command-injection-vulnerability-in-some-hikvision-products/
