“Spread-spectrum”, “Carpet-bombing” or “Sprayed” DDoS attacks are not new to the cyberthreat landscape. In recent weeks we have seen a significant increase in the occurrence of attacks using these techniques, especially in “gaming” environments which is often a reliable indication that they will become much more common in other verticals. This specific type of DDoS attack vector targets hundreds or even thousands of victim IP address at the same time. Typically, most traditional DDoS attacks only target a single victim IP address. Spread-spectrum attacks are more difficult to detect and mitigate.
Let’s analyze a few of these attacks that Corero successfully mitigated and see what differentiates them from the crowd.
Looking closely at the vectors of the attack we found examples with the following characteristics:
- Targeting an address range with 255 (/24) or even 4096 or 8192 victim IP address (/20 or /19)

- They are usually observed arriving from a botnet with the appearance of hundreds or thousands of members. (large but finite number of source IP addresses)

- The volume of traffic that each IP receives within the victim range is relatively small (approximately 500 Mbps)
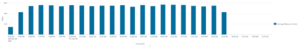
- The rate of traffic to each victim is similarly modest (100,000 pps)
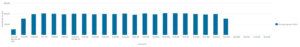
We observed cybercriminals using random source ports in combination with a destination port commonly used by games to try and emulate legitimate traffic (often simulating a widespread gaming protocol). This makes it more likely to get through border firewalls and more difficult to differentiate malicious packets from real traffic. It is very likely that programmed Botnets are being used to launch this attack and they are able to spread the attack traffic widely and evenly across the various IP addresses within the ranges that are being targeted. Many legacy detection mechanisms are oriented towards looking for a single DDoS victim IP address and these sprayed attacks appear to be able to avoid traditional one-victim-at-a-time detection and defense mechanisms in a manner analogous to flying under the radar.
- In aggregate, the total volume of the attack can reach large amounts. We have observed attacks of the order of hundreds of Gbps. The result is millions of requests that look like legitimate traffic adding up to completely saturate the victim’s network by skipping most of the protection methods that are typically focused on protecting individual assets or services and completely blocking access to services to all users.


- Although we have seen some cases where an attack has lasted several days, these sprayed attacks usually last just a few minutes, which makes detection and mitigation speed critical for effective DDoS defense.

Therefore, the requirement is for fully automatic protection that can detect and mitigate attacks in real time, across wide victim address ranges, while providing a complete view of what is happening on the network.
