It has become much more difficult for IT security teams to stop distributed denial of service (DDoS) attacks with a manual or Do-It-Yourself (DIY) approach, because cybercriminals are now using increasingly sophisticated techniques. Firewalls, routers and human security analysts are simply no match for modern DDoS attacks. One reason is that many attacks are so small, relative to legitimate traffic, that they often go undetected by security analysts; even if they do notice them, they can’t react quickly enough to mitigate them before damage is done. However, a new and rapidly growing challenge to legacy DDoS protection is the use of multiple vectors in the same attack. Even if such an attack is detected, the rate at which the vectors are changed ensures that legacy and manual solutions cannot engage mitigation fast enough to prevent its damaging effects. Recent Corero DDoS research shows that organizations are now consistently defending against eight or more vectors used in the same attack, often deployed over the course of only a few minutes.
Cybercriminals can, and often do, dynamically and automatically change parameters and vectors in response to the cyber-defenses they encounter. They often increase the number of vectors to build the volume of an attack. Sometimes they layer different vector types and sometimes they vary the attack vector itself to evade detection. When criminals continually modify the attacks, it becomes much more difficult to mitigate them. They often start with one vector, such as a simple UDP flood and, if unsuccessful, they try a second technique such as a DNS flood. Human security analysts can try to constantly reconfigure their defenses in response to varying vectors, but that manual approach is a daunting and, ultimately, impossible task. A manual, reactive approach simply isn’t good enough; it adds latency and inaccuracy to the mitigation process.
More importantly, DDoS attacks are increasingly automated; there is no way humans can compete effectively against automated, multi-vector attacks. The automated attack technology recognizes if it is successful and reacts in real-time.
The most common contributors to multi-vector attacks continue to be volumetric UDP amplification vectors including DNS, NTP, Chargen, SSDP and CLDAP. Multi-vector attacks present several additional challenges for detection and mitigation:
- For complete DDoS mitigation it is necessary to recognize each and every vector and respond with the appropriate mitigation, without impacting legitimate traffic.
- Multi-vector attack rates are usually additive in terms of bandwidth and packet rate. The total attack rate will be the sum of vector1 + vector2 + vector3, etc.
- Multi-vector attacks often exhibit more variability in attack rate during the attack period as different vectors join and leave the multi-vector attack. This presents challenges for many traditional detect and redirect DDoS solutions that typically provide partial mitigation capacity. Making a decision on the mitigation method (e.g. redirection vs. blackhole) based on the current attack rate is flawed as it can vary on a minute by minute basis.
- Attackers frequently mix resource exhausting TCP SYN floods from spoofed sources to make tracking more challenging.
- These vectors and more variants are added or subtracted multiple times during a typical 10-minute attack period. The aggregate amplitude may vary up to 10x during the attack as vectors surge and fade.
The image below is a snapshot from the Corero Security Operations Center (SOC) showing a typical multi-vector attack. This shows eight vectors used in this particular attack, but many other types of vectors can, and are, used.
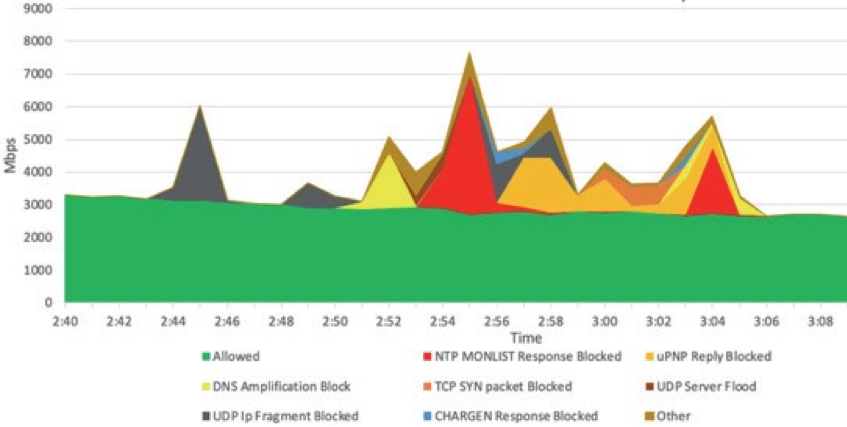
The only way to successfully defend against automated, multi-vector, attacks is to use an always-on DDoS protection solution that automatically and immediately detects and blocks DDoS attack vectors of all types, and sizes, in real-time. Such protection requires no manual intervention to detect and mitigate close to 100% of DDoS attacks before they enter a network. Organizations can virtually “set it and forget it,” thus reducing the need for security analysts, and giving existing IT security staff more time to detect and mitigate other cyber threats.
Corero has been providing state-of-the-art DDoS protection solutions for more than a decade to hosting providers, Internet service providers, managed security service providers and enterprises worldwide. To learn more about how to stop DDoS attacks, contact us.
