
Table of Contents
What is the Masjesu Botnet?
When discussing DDoS botnets, Mirai often comes to mind as one of the most notorious botnets responsible for record-breaking attacks. Since its source code was made publicly available, numerous Mirai variants have emerged, built upon the original code with various modifications. Recently, Eleven11bot and GorillaBot – Mirai-based botnets – have gained attention for their aggressive propagation and massive volumetric DDoS campaigns.
In contrast, Masjesu appears to have been developed independently rather than based on Mirai’s architecture. The operator behind Masjesu continues to actively promote DDoS-for-hire services via Telegram. The botnet reportedly supports attacks reaching up to 300 Gbps or 200 million packets per second (PPS), making it a serious threat in the DDoS landscape. This publication will focus on examining Masjesu’s DDoS attack methods.
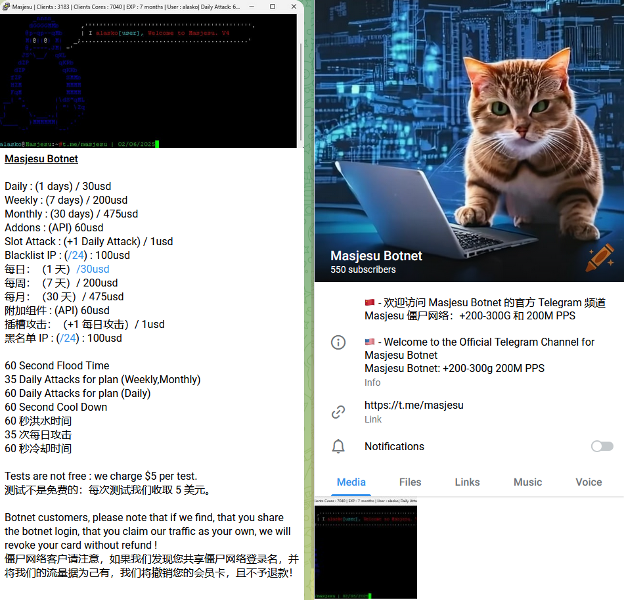
Figure 1: Masjesu telegram channel
Attack Methods
Upon analyzing the malware binary, we identified a function named Methodinit. Once a command is received from the command and control (C&C) server, this function is responsible for parsing the message and dispatching it to the corresponding attack method.
The supported attack methods include: udp, handshake, vse, gre, rdp, ospf, icmp, igmp, protorand, tcp_syn, tcp_ack, tcp_ackpsh, and http.
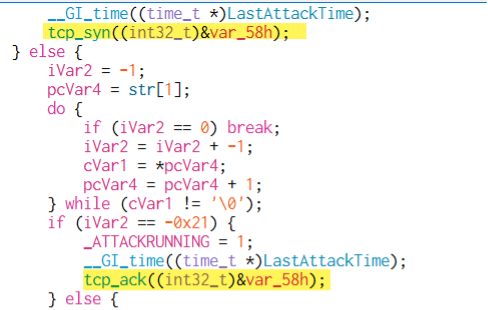
Figure 2: Methodinit function
UDP Flood Method
In this flood attack method, the random number generator is initialized using srand(time(NULL)) to seed it with the current timestamp. The rand() function is then utilized to generate randomized values for packet payload, destination ports, or packet lengths.
At address 0x0804a9ea, the function calls rand() to determine the size of 64 payloads, subsequently filling each one with randomly generated bytes. This approach introduces variability in the attack traffic, making it more difficult to filter or detect using signature-based defenses.
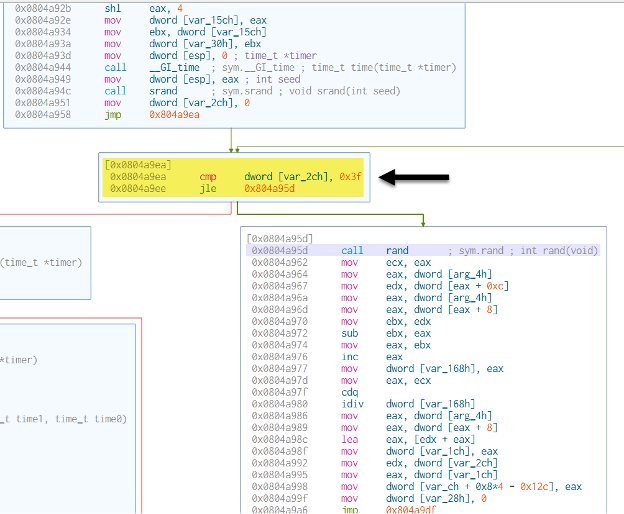
Figure 3: UDP method – 64 randomized chunks of payload
The bot then creates a UDP socket, sends the randomized packets to the target IPs and ports, and subsequently closes the socket.
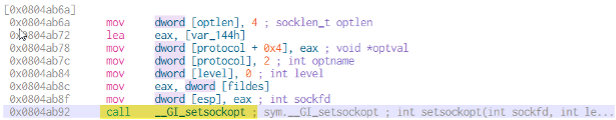
Figure 4: Create UDP socket
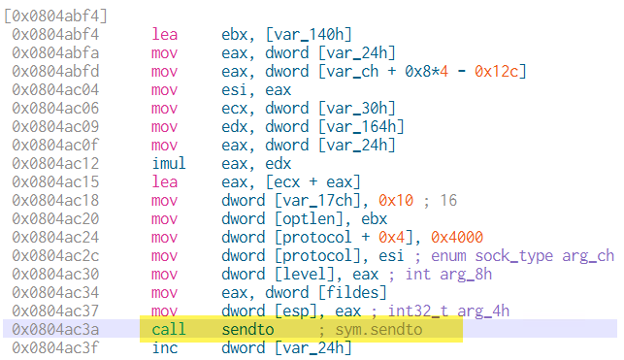
Figure 5: Send out the packets
The attack floods the target with UDP traffic for a configured duration. According to information from the associated Telegram channel, the default duration for each attack is typically 60 seconds.
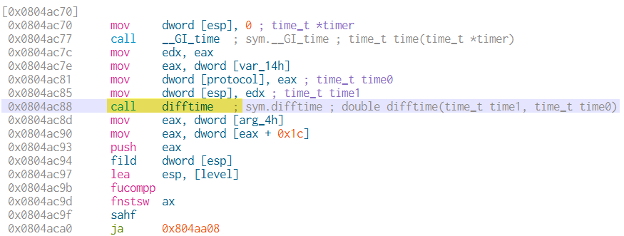
Figure 6: difftime function to break out the loop and stop the attack
TCP SYN Flood Method
While the overall structure of packet crafting and traffic transmission remains consistent, this method introduces additional logic to properly construct TCP packets. It involves building a valid TCP header, assigning a randomized source port and sequence number, and calculating a correct checksum for the final packet data.
The following function is responsible for setting the TCP flags specifically for a SYN packet. It ensures that only the SYN flag is set (bit = 1), while all other TCP flags are cleared (set to 0).
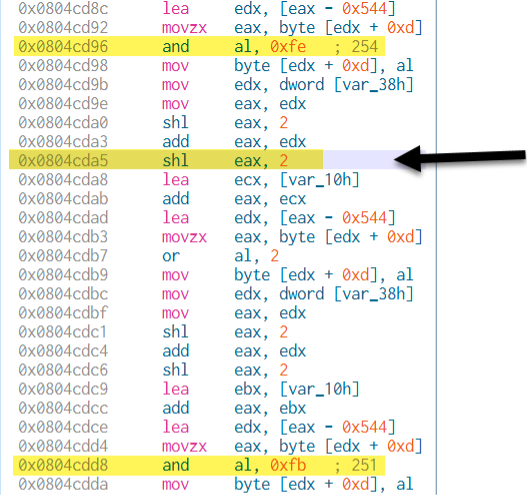
Figure 7: Set SYN flag to 1 and other flags to 0
The default TTL (Time-to-Live) value is set to 128(0x80), but it can be randomized within a range from 30 (0x1e) to 220 (0xdd + 0x1e), or it can be set to a user-provided TTL value.
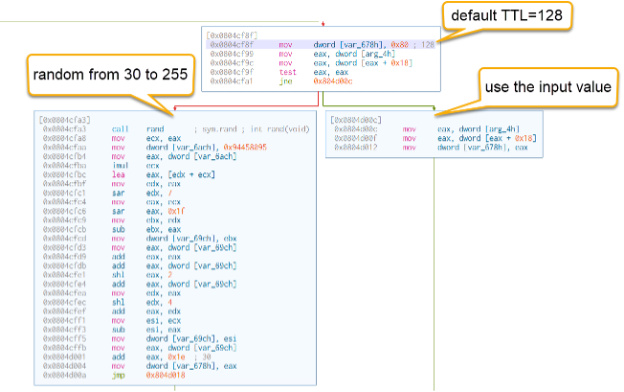
Figure 8: TTL
Closely examining the setsockopt() function, we observe that the IP_HDRINCL option is set. This instructs the operating system that the program will provide its own IP header. For IP address spoofing to occur, this option must be enabled, as the system would otherwise prevent modifications to the source IP address. This confirms that the method has the capability to spoof IP addresses.
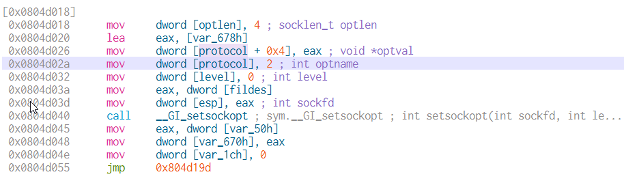
Figure 9: IP_HDRINCL is set in setsockopt()
HTTP Flood Method
An HTTP flood is a Layer 7 attack that targets a web server by flooding it with HTTP requests. Before sending data packets, a TCP connection is established. If the connection fails, the socket is closed, and no further data is transmitted. However, if the connection is successful, the bot enters a loop, continuously sending HTTP requests in an attempt to exhaust the server’s resources.

Figure 10: Connection attempt to server
The HTTP header is crafted with some pre-defined values and tries to simulate browser-like traffic at high volume.
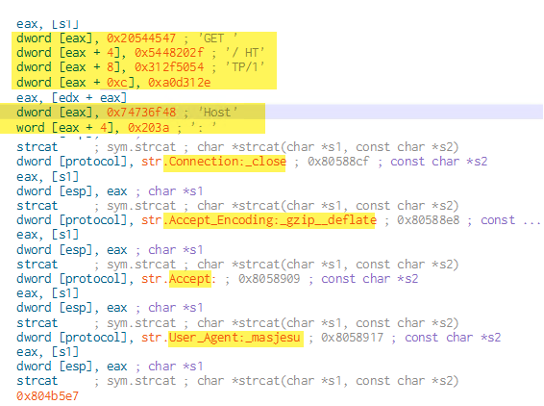
Figure 11: HTTP request header
Conclusion
Masjesu is a relatively new entrant in the botnet family. Its primary focus is launching a DDoS attack, and it has been actively promoting its services on Telegram. The botnet shows a clear effort to make DDoS traffic harder to detect and mitigate by randomizing packet headers and payloads, or by mimicking legitimate user traffic – making it increasingly difficult to distinguish between malicious and normal traffic. Additionally, Masjesu appears to be highly active; in our HoneyNet environment, within a span of only a few hours, a single bot was recorded initiating thousands of attack attempts.
Our DDoS Intelligence Service plays a crucial role in defending against modern DDoS campaigns by equipping organizations with the tools and intelligence needed to proactively detect, respond to, and neutralize threats. By continuously monitoring and analyzing global threat data, the service offers real-time insights into emerging attack vectors, tactics, and trends. This empowers organizations to strengthen their defenses through targeted countermeasures, reducing potential downtime, financial losses, and reputational damage.


